Physical Identity and Access Management Software
SecurityOS is a powerful physical identity and access management solution that bridges the gap between traditional access control systems and visitor management systems. It offers organizations an easy way to grant access credentials to guests using automated, rule-based workflows boosting control and visibility.
Grant Access Based on Requirements
Create personalized permissions to precisely define who can access specific facility areas. Set exact times and durations for guest access based on individual requirements.
Automate Access
Streamline and automate building access for visitors with rule-based workflows.
Control Points of Entry
Provide an easy, secure and reliable way to manage physical access to your facility for visitors, contractors and other temporary guests.
Enhance Visibility with Real-Time Reporting
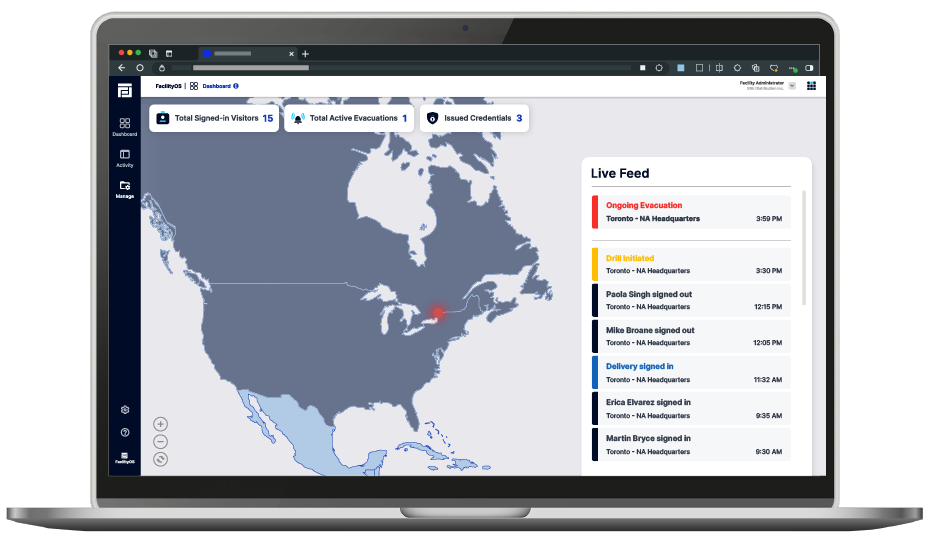
Gain enhanced security and visibility with a complete log and analytics of temporary visitor movements and access.
See SecurityOS in Action
Find out how you can extend the benefits of access control to visitors and contractors.







Streamline Temporary Credential Management
Manage the Flow of People – Beyond Employees – In Your Facility
Easily extend your access control systems to manage visitors, contractors, and temporary guests with automated, rule-based workflows. This ensures you can issue credentials efficiently while maintaining a secure environment.
Reduce Resource Demands and Save Time
Eliminate the need for visitor escorts by automating credential provisioning. This reduces operational costs and allows your team to focus on what matters most, increasing productivity across the board.

Efficient & Secure Access Issuance
Enhance Security
Reduce dependency on authorized personnel by automating access issuance, ensuring secure and error-free processes. This enhances site security and reduces the potential for costly mistakes or delays.
Minimize Risks
Streamline and secure your access issuance process with rule-based workflows that minimize human error and ensure timely, compliant credentialing for visitors, contractors, and temporary employees.

Increase Control and Visibility
Control Points of Entry
Manage exactly where visitors can go, how long they can stay, and when they can access specific areas. This ensures tight control over your facility’s entry points, enhancing security and operational efficiency.
Comprehensive Reporting
Monitor visitor access across your entire business in real time. Track who accessed which entry points, when, and review a complete history of issued credentials for comprehensive oversight.
Be Audit Ready
Maintain digital audit logs of all issued credentials, both current and historical, to stay prepared for safety audits. Effortlessly monitor the usage of temporary credentials and ensure compliance with security standards.

Why Do Organizations Need a Physical Identity and Access Management System?
Large numbers of compliance related activities and building access are attributed to temporary employees, visitors, and contractors. Traditional Access Control systems offer enhanced property security, granting staff facility access while denying access to unauthorized individuals, but they are not designed to support these temporary credentials and dynamic use cases.
That is where SecurityOS comes in. It enhances Access Control systems to support these complex requirements by enabling access control management for visitors, contactors, and temporary employees.
Contractor Compliance Management Features and Benefits

Control Who Gets Access
Rest assured that guests are only granted access to your facility when and where it’s required. Create personalized permission sets to specify which access points to include, when access is active (which days and times), and the duration of time access will be granted (start and end dates).

Automate Provisioning
Issuing access is time-sensitive, error-prone, and cumbersome, requiring specific authority and posing risks if not handled properly. Remove ambiguity around who gets access to what, eliminate human error and increase security with rule-based automation. With SecurityOS, you can use workflows to automate identity lifecycle management and permission provisioning for facility visitors when signing into VisitorOS.

Extensive Reporting
Gain visibility over the movement of temporary visitors within your facility with a complete digital log of all current and historical credentials issued. See access logs for access points, access levels by person and more. With comprehensive physical security analytics, SecurityOS allows you to track and monitor the usage of temporary credentials giving you visibility into who is accessing your space.

Expire on Sign-Out
Optionally choose to configure visitor access tags to expire on sign-out. Alternatively, set permissions to automatically expire after a set amount of time.

Centralized Management
Streamline operations and save valuable time with SecurityOS. With a centralized system to manage and administer temporary credentials across multiple locations or facilities, Administrators have complete visibility across their entire business.

Control Points of Entry
Use your FacilityOS provided hardware or integrate with third-party access control systems to control points of entry such as doors, turnstiles, gates, elevators and more. SecurityOS is not a replacement for access control – it extends the benefits for complex, dynamic requirements.

Data Privacy and Compliance
SecurityOS adheres to data privacy regulations and industry-specific compliance requirements, safeguarding personal information collected during the temporary credential management process.

Intuitive, easy to use
We rolled out 90 locations quickly in about 3 months with the help of iLobby's support team.
Jeff O.
Field Service Leader


iLobby is EXCELLENT for contractor management!!
even used the iLobby system to warn us if contractors had not left the site after a certain period of time, but typically should have.
Dee M.
Health Safety Environment Coordinator


I highly recommend iLobby
Knowing who is at your facility and having the ability to alert them to evacuate if necessary is exceptionally beneficial.
Todd C.
EHS Manager


iLobby runs itself
instance viewing of everyone coming and going plus add visitors in advance.
Robert I.
IT Automation Technician


Ton of features
Solved our problem of maintaining annual paperwork for rules and regulations for visitors and contractors.
Nicole F.
Food Safety and Quality Assurance Manager


“Great Experience”
A lot more robust & easier to navigate than paper. Emergency notices are also a big feature that we use in the case of emergencies at our sites to communicate to our employees.
Travis E.
IT Plant Support Analyst, Infrastructure & Security


“Extremely Versatile”
This software allows us to notify our employees in case of emergency all with one simple set up per employee.
Jennifer A.
Manager, General Services Lactalis USA


"iLobby is EXCELLENT for contractor / visitor management!!"
The iLobby system is easy to use, the software is user friendly, and there are multiple ways to take advantage of the capabilities of the system.
Dee M.
Health Safety Environment Coordinator


"Ease of implementation and use."
Visitors have been impressed with how easy and advanced our Check-in process is.
Chad J.
Director of Supply Chain


"Definitely recommend"
We have experienced zero issues with visitors checking in which is all you can ask for with a visitor mgmt platform!
Molly V.
Executive Assistant, Operations


"Easy set up, easy to use"
Its easy to use, very customizable and was very quick and simple to implement.
Billy L.
Building Automation Systems Manager


"A very user friendly product!
We had a very easy time implementing this as our visitor management solution.
Usama M.
IT Supervisor, Plant Support

Safely Manage Visitor Access
Safely managing access for visitors is a blind spot for many organizations. SecurityOS gives you complete visibility into visitor movement onsite.
Issue Daily Credentials
Set up credentials such as day passes for visitors, contractors or temporary workers, which automatically expire upon sign-out. Prevent the re-use of credential by enforcing daily sign-ins.
Grant Recurring Access
Issue recurring credentials for specific access points, such as for a head office employee working from your facility for the month, or service people needing entry to a machine room every two weeks. Credentials remain valid for a predetermined duration before requiring renewal.
Issue Credentials for an Event
Provide credentials to visitors coming in for an event. Facility access remains active for the event duration and expires automatically on completion. Sign-in is enforced at the initial visit and credentials can then be reused for the remaining time.
Issue Credentials Manually
Set up credentials on the fly for an employee who forget their access card. Email a QR code that can be used to gain access for the day allowing in and out for the day without signing in to your Visitor Management System.
What is a Physical Identity and Access Management System?
A physical identity and access management system (PIAM) manages the access rights and physical identity of individuals. It is used to securely issue, track and mange temporary physical facility access for visitors ensures only authorized individuals are granted physical access to the defined space. A PIAM system not only streamlines and automates permission provisioning, it also enhances safety and security while increasing control and visibility.
How Does a Physical Identity and Access Management System Work?
Step 1
Configure Profiles and Access Levels
Administrators pre-define permission sets to map out where and when visitors will be granted physical access to your facility. You can specify when access is active, for how long and for which points of entry. Workflows are set up to automatically attribute permissions based on visitors meeting the specified criteria.
Step 2
On-Site Check-In
A visitor arrives on-site and signs in at a VisitorOS kiosk.
Step 3
Credential Issuance
SecurityOS then verifies the visitor’s identity and issues credentials based on the workflows set up by the organization and physical access is granted to authorized visitors.
Step 4
Analytics and Reporting
Access a digital audit trail of credentials issued, a list of successful activities at each access point, along with a real-time view of facility access. SecurityOS maintains a digital audit trail of who accessed which entry point at what time for compliance requirement and seamless incident resolution.
Who Benefits from a Physical Identity and Access Management System?
Facility Manager
Facility managers gain precise control over who can access specific areas, how long they can stay, and when they can enter. This ensures operational efficiency and tightens security by managing designated access points and permissions centrally.
Security Teams
Security teams enhance safety with automated, rule-based workflows that minimize human error and ensure compliant credentialing. Real-time reporting and digital audit logs provide comprehensive visibility into all movements, reducing risks of security breaches.
Visitors
Visitors receive efficient, hassle-free access through personalized, temporary credentials. Automated provisioning reduces wait times and confusion, enhancing their experience while maintaining security.
Contractors
Contractors benefit from seamless, rule-based access to the areas they need, during specific times, without unnecessary delays or miscommunications. This improves their productivity and satisfaction.
Ready to Learn More About SecurityOS?
Request a demo to see how SecurityOS can deliver immediate results for your organization.
Book a Demo