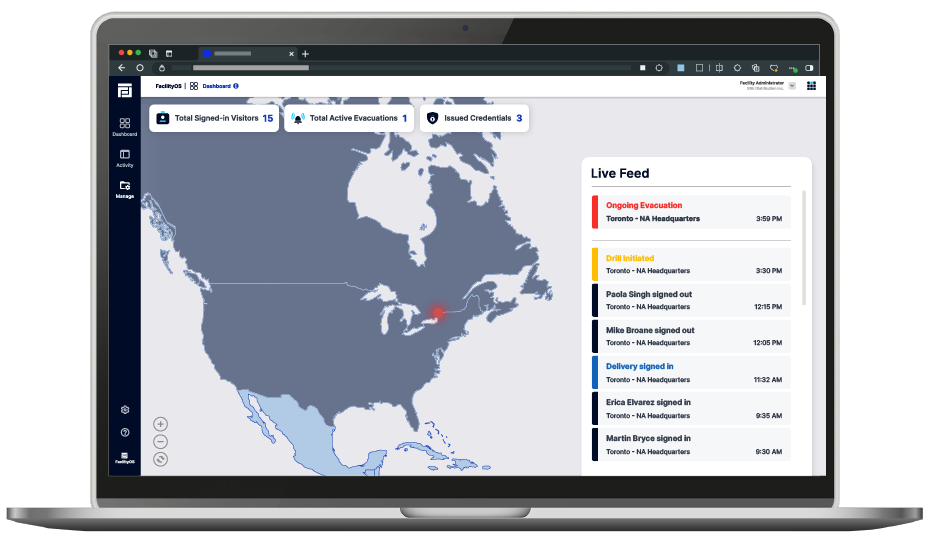
FacilityOS > VisitorOS > Approve/Deny Visitors
Approve/Deny Visitors

Streamline Access with Automated Control
By automating the approval process through a custom configuration, you ensure compliance with regulatory requirements while minimizing manual intervention. This feature protects your facility and streamlines the visitor experience, ensuring only authorized visitors gain access.
ITAR Compliance
Meet International Traffic in Arms Regulations (ITAR) by ensuring that only eligible visitors can access sensitive areas. Controlling visitor entry is an essential safeguard that enhances security in regulated environments, protecting valuable assets and information.
Verify Visitor Documentation
Verify that visitors possess the necessary documentation to be on-site, such as citizenship verification for U.S. facilities. This step ensures compliance with legal and regulatory standards, protecting your organization from potential liabilities.
Confirm Visitor Identity
Add a critical checkpoint in the process, allowing facility personnel to verify that the person who signed in matches their identification. This extra layer of scrutiny is particularly vital in high-security environments with high stakes.
Control Visitor Access
Only approved visitors enter your facility, preventing unauthorized individuals from accessing your premises. This control enhances overall security and ensures a safe environment for your staff.
Mitigate High-Risk Access
With watchlist integrations, you can prevent high-risk individuals from entering your facility. Screen individuals in real-time against watchlists, bolstering your security measures.
Comprehensive Audit Logs
Have access to full audit logs that track visitors who were approved and denied entry. This transparency aids in compliance reporting and helps maintain accountability within your visitor management process.







How Approve/Deny Works
Designed for quick and efficient visitor monitoring, watchlists allow organizations to automatically screening visitors against a lists during the sign-in process. Seamlessly integrate with third-party watchlists or optionally build your own internal lists, facilitating real-time identification of potential threats. With customizable alert settings, watchlists help to elevate security tailoring the monitoring experience to each organization's specific needs. Automate visitor monitoring, enhance security, and modernize the surveillance experience with VisitorOS.
Step 1
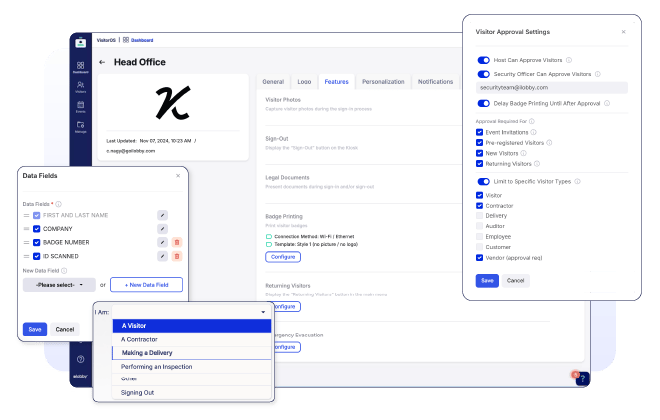
Set Up a Custom Configuration to Suit Your Organization’s Needs
Set up the criteria for approving or denying different visitor types according to your organization's entry guidelines. Additionally, you can designate which employees can grant approvals or denials. This custom configuration can ensure an automated workflow for handling visitor check-in requests for approval or denial. Do you have a list of potential guests for an upcoming event? Set up an advanced approval or denial process for potential attendees before sending out the invitations.
Step 2
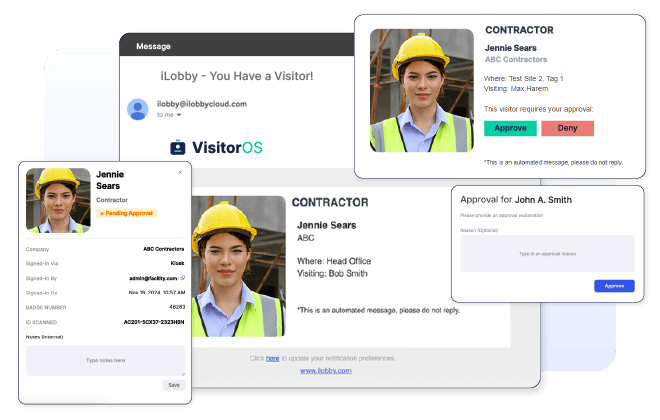
Validation of Entry Request
When a guest signs in on-site that meets the predefined criteria to trigger an approve or deny check, VisitorOS automatically sends a request to the designated representative for verification. From there, the designated representative will approve or deny the visitor based on your organization’s guidelines. When a visitor is invited or attempts to sign-in, an approval request is sent to designated personnel for verification.
Step 3
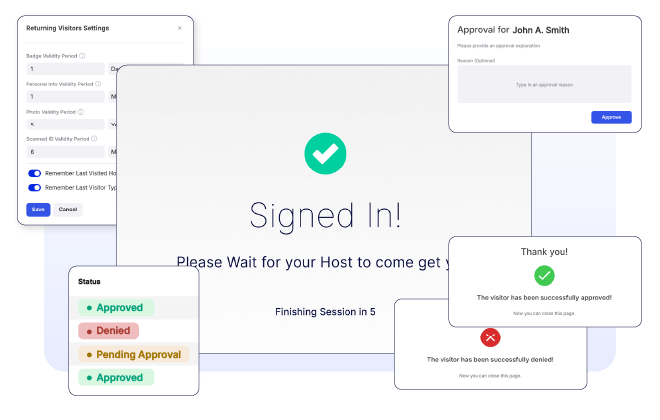
Visitor is Approved or Denied Entry
The visitor is either approved or denied entry to the facility. In the case of denial, administrators receive prompt email notifications, enabling quick responses and adherence to security protocols.
Step 4
The Record is Tracked in the Visitor Log
Every approval and denial are recorded in the visitor log, providing a comprehensive history of who was granted entry to the facility, who was denied entry to the facility, and when. This tracking mechanism is essential for maintaining security oversight.
Who Benefits from Approve/Deny Functionality?
The approve/deny visitors feature is designed for organizations prioritizing facility security and compliance.
Security and Compliance Officers
Security and compliance officers benefit from streamlined processes that help them enforce regulations and maintain a secure environment. The feature provides them with tools to monitor visitor access effectively.
High-Security Environments
Organizations operating in high-security environments can leverage this feature to ensure that only vetted individuals gain entry. This capability is crucial for safeguarding sensitive areas and protecting valuable assets.
Compliance-Certified Industries
Facilities requiring compliance with standards such as ITAR, CGP, and other regulatory certifications benefit significantly from this feature. It aids in meeting stringent requirements while enhancing overall security management.
What Can VisitroOS Do for You?
Request a demo to see how VisitroOS can deliver immediate results for your organization.
Book a Demo